Browser Password Scraper – Instant Credential Extraction from Live Systems
During a recent on-scene search warrant triage, we faced a familiar challenge: two locked mobile phones with no clear path to access. One was the primary target device, and the second was potentially related. Neither could be brute-forced or bypassed with available tools. Thankfully, an unattended Windows PC at the scene was still unlocked when we arrived.
We began manually sifting through the browser’s saved passwords, hoping to find clues. It was slow, clunky, and frustrating—but ultimately successful. A saved browser credential provided the pincode to unlock the second phone. That device then led us to additional passwords—one of which unlocked the first phone. The data recovered was crucial, and the case likely would have stalled without it.
That incident inspired this tool.
🔍 Introducing: Browser Password Scraper
Browser Password Scraper is a self-contained, Windows-only executable designed for forensic examiners to rapidly extract saved browser passwords from live systems. With a single click, it scans and collects credentials from all supported Chromium-based browsers—including Chrome’s newer v20 App-Bound Encryption—as well as from Firefox’s secure credential store.
No need to manually navigate settings screens, supply user passwords, or hunt through SQLite files. The script performs a complete extraction in seconds—and formats the data into clean, readable CSVs.
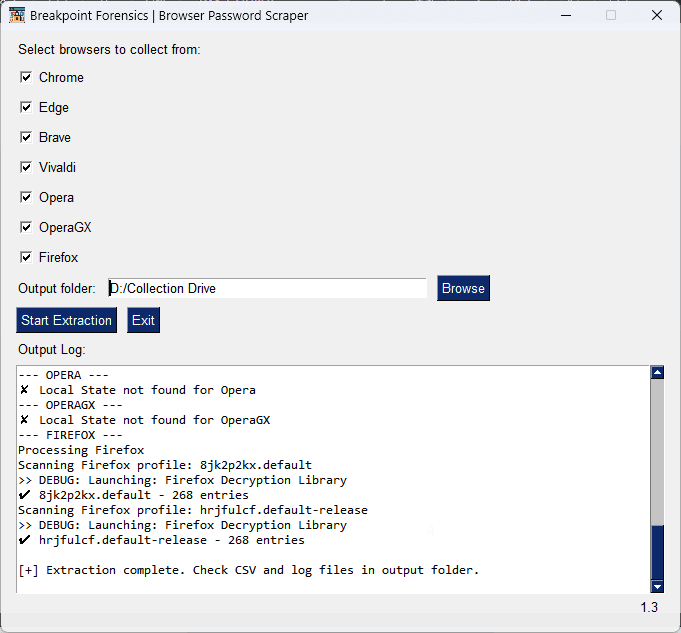
⚙️ Key Features
- ✅ Self-contained EXE (no dependencies or installs required)
- 🔐 Broad Chrome-Based Browser Support
- Both v10 (legacy DPAPI) and v20 (App-Bound Encryption) formats
- 🦊 Full Firefox support via automated extraction
- 📄 Clean CSV exports by browser and profile
- 🧠 No user PIN/password required to access stored browser credentials
- 🚫 Bypasses GUI restrictions where manual viewing would fail
- 🧪 Ideal for live triage and lab review
- 🧼 Temporary working directory auto-cleans after use
🔍 Why It Matters in Forensics
In modern investigations, suspects often use strong mobile device passwords and biometric locks that can’t be bypassed easily. However, those same users often reuse or store those credentials on secondary devices—most commonly their Windows computers.
Whether in the field or back in the lab, this tool gives you a fast, automated way to check those systems for saved credentials—without relying on decrypted disk images, which won’t expose browser passwords unless live collection is performed on a running and logged-in OS.
💻 Supported Browsers and Encryption Types as of Initial Public Release v1.3
Chromium-Based Browsers
(Detects and handles v10/v20 automatically where applicable)
- Google Chrome
- ✅ v10 (DPAPI)
- ✅ v20 (App-Bound Encryption)
- Microsoft Edge
- ✅ v10 (current)
- Brave
- ✅ v10
- Vivaldi
- ✅ v10
- Opera / Opera GX
- ✅ v10
Mozilla Firefox
- ✅ Native support
- 🔐 Extracts without requiring Primary Password entry
📝 Note: Chrome v20 uses a newer App-Bound encryption mechanism that prevents standard decryption. This tool includes embedded fallback support via direct process memory injection, bypassing the need for complex setups or separate decryption steps.
🧰 When to Use It
- 📍 On-scene triage when the target device is live and unlocked
- 🧪 In the lab using booted clones or mounted VMs of seized drives
- 🔍 As a supplement to forensic image analysis—especially when decrypted credentials won’t otherwise be recoverable
- 🚓 During live preview/search warrant collections, before the machine goes offline or reboots
⚠️ Important:
- This tool must be run under the target user’s logged-in session to access protected credentials.
- Antivirus software may flag components due to injection techniques used for v20 decryption. We strongly recommend disabling AV during collection to avoid missed data or failures.
- Run the tool from a connected forensic USB drive—do not copy it to the suspect machine.
✅ Download
Download:
Browser Password Scraper
MD5:
👨💻 Final Thoughts
Whether you’re on-scene or working in the lab, Browser Password Scraper fills a vital capability gap for modern digital investigations. It’s fast, portable, and doesn’t require installation, login credentials, or scripting experience. More importantly—it helps you pivot quickly in cases where traditional password recovery methods fall short.
We’re releasing this tool free for the forensic community. Let us know how it works for you, and what you’d like to see next.

