
Multiplatform DFIR Live Triage and Collection Tool
Requirements and Tested Platforms:
- Windows (X64) Versions: 7, 10 or 11
- MacOS 11.7-12.6 (Intel X64 or M1-ARM))
- Ubuntu 20.04 -22.04(X64)
Download:
Current Version: 1.3.7 – 01/02/2023
FileSifter(MacOS) 3e43c535fec3d68ffedca4f15ec6ba15
FileSifter(Linux) 35653d2453875033b5fd398d46813723
FileSifter - User Manual 4f3240337b90b1adfd954f5a5e0a65e4
About
FileSifter is a digital forensics live-triage collection tool designed for deployment across multiple OS platforms including Windows, MacOS, and Linux.
The portable tool is meant to offer a means of efficiently triaging the contents of a running computer, its hard drive, or any other storage device and its associated file-system. Ideal scenarios where this might be employed is in situations where the computer or device might be encrypted and can’t be shut down for a typical dead-box examination of the storage device.
In these situations, an examiner would historically be limited to conducting a live acquisition of every file on the computer or storage device. While this might be effective, it can significantly increase the time it takes to review the contents of a device, as the examiner has no real-time feedback as to the contents of the device. Additionally, critical time might be wasted as data is being collected that may not be relevant. These are some of the situations that File Sifter is designed for.
Primary Features
-Live File Collection to either ZIP or TAR packages.
-Keyword Filtering function. Allows import of custom keyword dictionary file that when enabled will only collect files with match in keyword list.
-Easy targeting of files/folders to be collected using simple user interface and case setup.
-Support for targeted collection of Image, Video, Archives, and/or Documents and packaging into VICS JSON evidence package for easy import and review into tools such as Griffeye Analyze.
-Automatically generates CSV report for all files collected storing original metadata such as MAC times, paths, etc.
-Forensically sound. When FileSifter is executed from a forensic collection drive, program data, reports, and other generated data is only saved to the examiners connected drive.
Setup
File sifter is packaged and distributed in 3 current versions covering Windows, MacOS, and Linux executables.
As the tool is designed to be executed as a Live Triage Tool, its executable requires no ‘installation’ and runs as a portable application.
Setup only requires copying the appropriate executable to an examiners collection drive, where it is then executed from.
All collected files will automatically be stored on this collection drive or wherever the FileSifter executable is located.
Main Interface
Case Setup
FileSifter organizes collected data based on a Case# and Item# schema. Simply enter the appropriate identifiers in the Case and Item fields.
Collection Mode
FileSifter comes with two primary collection modes. They can be executed individually, or combined and run at the same time.
Add Files to Archive
When selected any files identified for collection will be added to an archive file on your collection drive.
Current archive formats include ZIP or TAR.
Create VICS JSON Package
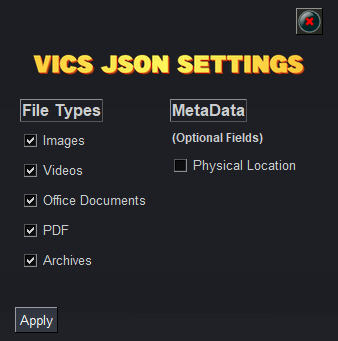
When selected any files identified for collection will be added to a VICS JSON evidence package, and a VICS compliant JSON will be built.
This JSON package can then be imported into a tool such as Griffeye or any other tool supporting VICS evidence packages for efficient review of media data.
Keyword Filtering
If keyword filtering is enabled, the user is prompted to provide a text file containing keywords relevant to the exam, investigation, etc.
This will then limit the collected files to only those with a keyword match.
If a keyword match is found in the path or filename of a file, the file will be collected and added to the collection container/archive file. The file will also be processed for relevant metadata, and its MD5 hash-value computed.
File Metadata and VICS/CSV Output
Data recovered and imported using FileSifters VICS JSON Package and logged in the generated CSV, will collect and fille several metadata fields, and may vary depending on OS and Filesystem formats.
These will include but are not limited to the following:
SourceID: Based on Item# Field
Mime Type: Identified File Type Based on Extension
File Name/Path: As located on target item.
Create/Written/Accessed Timestamps: The timestamps collect from the original target machine during FileSifter collection.
JSON Example:
CSV Example:

